FCI & CUI: Why Commercial Companies and Subcontractors Should Pay Attention
Even if your business is not a prime contractor or direct government vendor, you may still be required to safeguard federal information. Commercial companies that support primes or large integrators often inherit these requirements through flow-down clauses in subcontracts. Meeting them is critical to stay competitive in the supply chain.
Federal Contract Information (FCI)
What is it?
Information provided by or generated for the federal government under a contract is not intended for public release. Examples include contract terms, internal communications, and project specifications.
Requirements for Commercial Companies:
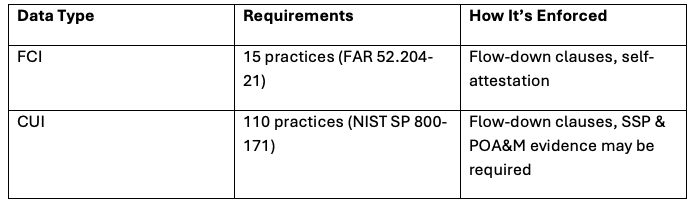
- Implement 15 basic safeguarding practices (access control, antivirus, patching, user IDs). Note that CMMC Level 1 (NIST 800-171) requires 17 controls.
- Based on FAR 52.204-21.
Access Control
- Limit information system access to authorized users, processes acting on behalf of authorized users, or devices (including other information systems).
- Limit information system access to the types of transactions and functions that authorized users are permitted to execute.
- Identify information system users, processes acting on behalf of users, or devices.
- Authenticate (or verify) the identities of those users, processes, or devices, as a prerequisite to allowing access to organizational information systems.
External Connections and Public Systems
- Verify and control/limit connections to and use of external information systems.
- Control information posted or processed on publicly accessible information systems.
- Monitor, control, and protect organizational communications (i.e., information transmitted or received by organizational information systems) at the external boundaries and key internal boundaries of the information systems.
- Implement subnetworks for publicly accessible system components that are physically or logically separated from internal networks.
Media and Physical Access
- Sanitize or destroy information system media containing Federal Contract Information before disposal or release for reuse.
- Limit physical access to organizational information systems, equipment, and the respective operating environments to authorized individuals.
- Escort visitors and monitor visitor activity; maintain audit logs of physical access; and control and manage physical access devices.
System Integrity and Protection
- Identify, report, and correct information and information system flaws in a timely manner.
- Provide protection from malicious code at appropriate locations within organizational information systems.
- Update malicious code protection mechanisms when new releases are available.
- Perform periodic scans of the information system and real-time scans of files from external sources as files are downloaded, opened, or executed.
- Compliance is self-attested — no third-party certification required.
Controlled Unclassified Information (CUI)
What is it?
Sensitive but unclassified data that must be protected under federal law or regulation. Examples include export-controlled data, defense schematics, critical infrastructure information, and sensitive health records.
Requirements for Commercial Companies:
- Must follow NIST SP 800-171 (110 security requirements across 14 control families).
- Required to maintain a System Security Plan (SSP) and Plan of Action & Milestones (POA&M).
- Compliance is typically self-assessed, but primes may request documentation or evidence before awarding work.
Snapshot for Commercial Companies
How Ekko Security Helps Commercial Companies
- Scope Your Data: Determine if you’re handling FCI, CUI, or both.
- Gap Analysis: Identify where your practices fall short of NIST 800-171.
- Policy & Documentation: Build your SSP and POA&M to satisfy prime contractors.
- Evidence Support: Prepare the artifacts that the DoD or civilian agencies will request during supplier onboarding.
- Continuous Compliance: Keep your business audit-ready year-round and prove trust to partners.
Don’t lose out on contracts because of compliance gaps. Contact Ekko Security at https://ekkosecurity.com to get started.
